
The Most Uncomfortable Vulnerabilities, the Least (or Incorrectly) Managed Risks & Recommendations for Today's Board of Directors
Introduction
Vulnerability. Threat. Risk.
In risk management, management and boards of directors talk a lot about, well, the risks – the probability of negative events and the scale of impact. But what about the vulnerabilities – the weaknesses, flaws and deficient designs and processes?[1] Post-mortems and root-cause analysis tend to be the driving forces behind vulnerabilities getting due attention.
That’s too late.
If boards understood better and management identified earlier certain vulnerabilities, companies would notch more "wins" in the preventative risk management column. They would avoid the risk altogether, rather than reducing, sharing, accepting or, worse, responding to the risk. That last one bears another name.
Crisis management.
Overview: The Most Uncomfortable Vulnerabilities
The following explains the most uncomfortable vulnerabilities existing for boards of directors today. It aligns with risks that are not being managed - either they are not getting the attention they deserve, or the efforts are off base.
This assessment is qualitative.
It is based on years in regulated financial services, risk management and board rooms. This includes enterprise risk, financial crimes, consumer protection and cybersecurity. It benefits from every shape and size of federal, state and foreign regulatory examination, discussions with peers and a deep appreciation of applicable and effective risk management versus the theoretical (think: regulation) and, many times, ineffective counterpart.
It acknowledges risks that tend to garner the most attention at the management and board level, be they de rigueur or just darn sexy (credit, interest rate, liquidity, financial crimes, cyber, data protection and, of late, geopolitical). But, the focus here is rooted in both the academic and operational desire to improve for boards of directors the full enterprise of risk management.
Intended Impact
Overseeing and managing these most uncomfortable vulnerabilities will materially contribute to an ongoing:
How to Read It
This article breaks down the vulnerabilities across six areas: Board of Directors, Executive (or Senior) Management, Employees, Customers, Technology and Operations. It then details the vulnerabilities before offering recommendations and considerations for the board and management that are practical, in a few instances audacious, but all realistic as to their material ROI. Lastly, it categorizes the vulnerabilities in their proper areas of Enterprise Risk Management.
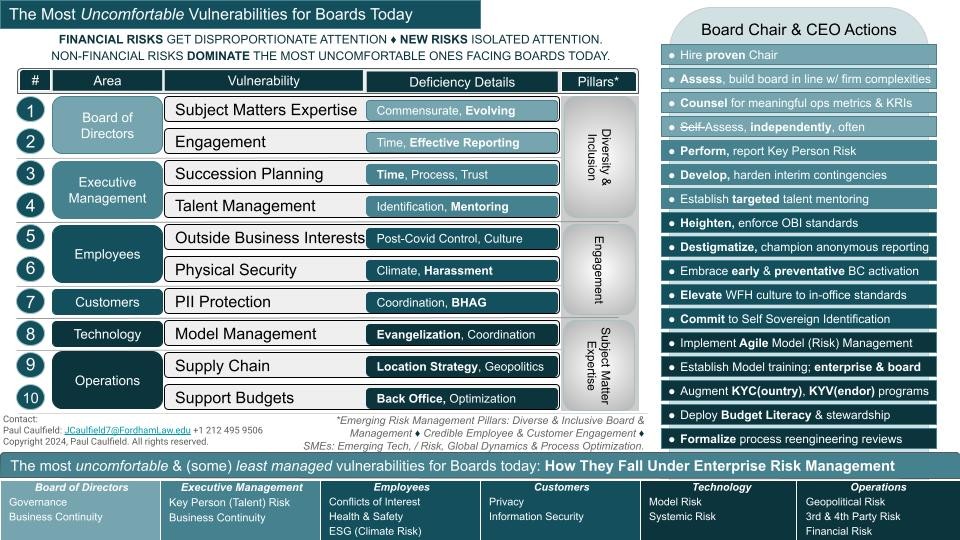
I. Board of Directors
The Uncomfortable Vulnerabilities:
Details: A board of directors is not the place for founders and chief executives to install friends, personal or even professional. A challenge corporate boards face is ensuring its makeup, its breadth of expertise, is commensurate with the company’s complexities, opportunities and risks. A recent example is cybersecurity. A more pressing example is models, AI and LLMs. Another challenge, the Achilles Heel with boards, is efficient reporting by management that properly harnesses the time, attention and guidance from board members.
How to address it: Hiring a proven board Chair is priority one. The Chair and chief executive (if they are separate roles) must undertake an objective assessment of the company’s makeup, utilizing its strategic plan and risk assessment, to ensure members are hired for the skills they bring and agnostic of their personal or professional affiliations with the company, founders, executives. Two, the Chair, at a minimum, must work with management to ensure reporting is board appropriate, concise, timely and complete as to performance, risks and opportunities.[2] Three, the Chair, from time to time, must insist on an independent assessment of board performance and composition as strategic plans and risk assessments evolve.
Risk Management Areas Addressed: Governance, Business Continuity
II. Executive Management
The Uncomfortable Vulnerabilities:
Details: Executives are not pre-wired to plan for their successors. A challenge for highly- or even well- functioning management is making time for and following through with key corporate roles succession. While a recent example is the eponymous HBO Max series, more pressing examples abound across small businesses. None compares to that at Disney, however. Another challenge, the Achilles Heel of management, is the presumption that mere elevation of employee to manager begets an innate ability to manage others effectively.
How to address it: Akin to the board Chair’s importance, empowering a proven Human Resource Executive is priority one. The HR Executive must undertake the responsibility of guiding the process, working with executives and management to identify the company’s key persons in financial and operational impact, starting with the CEO. Two, within this process, the HR Executive must ensure talent development plans, cross-training initiatives and contingencies are in place should the departure of the key person materialize. Three, the board must hold the CEO and HR Executive to account, for periodic updates as to these key persons, the risks their departures pose and the readiness of their successors and contingencies.
Risk Management Areas Addressed: Business Continuity, Talent Risk
III. Employees
The Uncomfortable Vulnerabilities:
Details: Boards are fully aware that remote working standards are nowhere near where they need to be. They may not be aware that working hours and locations are fungible, dress codes inconsistent and meetings poorly attended (in mind and body), over-subscribed and woefully inefficient. This has chipped away from in-office decorum, standards, productivity, and health and safety.
A challenge management faces is four-fold:
A recent example is the rise of the side-hustle. More pressing examples are workplace bullying and antiquated business continuity measures. The Achilles Heel is a post-covid malaise that continues to stymy coordination and resetting this critical dynamic.
How to address it: Board of director-level urgency is priority one. The Chair and chief executive must undertake the immediate and absolute reset of office culture, on site and remote. Two, they must commission a singularly focused Chief Conduct Risk Czar, named for the temporary but zeitgeist intended, empowered with her own immediate and absolute authority to communicate, educate, embed, champion and enforce heightened behaviors. While dress codes and meeting hygiene rank high, proper conduct involving conflicts of interests, employee trading (where applicable) and workplace harassment deserve primary focus. Three, two preexisting tools – anonymous reporting hotlines and, unironically, remote working – deserve renewed attention given their tangible values. Hotlines must be destigmatized and made readily accessible, and employee-wide remote-work plans must be activated sooner in the face of increasing extreme weather-related events.
Risk Management Areas Addressed: Conflicts of Interest, Health & Safety
IV. Customers
The Uncomfortable Vulnerabilities:
Details: While boards may think that consumer data protection is getting an appropriate level of attention across industries, it is not receiving the right or bold enough focus. The challenge and current Achilles Heel is strategy, given the proliferation of and varied federal, state and foreign regulatory requirements, the sheer size of PII that companies possess and the multitude of locations (i.e., systems) where these variable pieces of data reside. Recent examples are the billions of dollars in fines levied globally against the likes of Meta, TikTok, WhatsApp, Amazon, Google, DiDi, T-Mobile, Instagram, Capital One and Morgan Stanley. The current model is unworkable and, for the largest corporations and their shareholders, it should become an immediate, unacceptable cost of doing business. Boards of any size company should agree.
How to address it: A course correction, industry- and market-wide, is priority one. Higher than the importance of the board Chair and HR Executive outlined here, the (Chief) Data Protection Officer or equivalent must undertake a call to arms and be given the resources to beat a data protection path to the inevitable future of Web 3.0 and self sovereign identity (SSI). Two, this means a longer game, but one the DPO must bring to the board and chief executive’s attention and includes the interplay between blockchain technology, homomorphic encryption and zero knowledge, current industry players (there are many, but include Microsoft, Wipro and 1Kosmos), platforms such as Sovrin Foundation, use cases such as India’s Aadhaar program and compelling value proposition when it comes to anti- fraud, money laundering and identity theft measures that have long eluded global financial crimes risk management. Three, as opened, industries, not companies, and governments need to start banding together as Web 3.0 comes online.
Risk Management Areas Addressed: Privacy, Information Security, Operational Risk
V. Technology
The Uncomfortable Vulnerabilities:
Details: It is no longer acceptable for non-IT staff, especially management and boards of directors, to yield general and even moderate IT literacy to the Help Desk. A significant challenge these groups face is that stakes have risen: more advanced technologies are coming online, an emerging workforce is quickly adopting them, and not only are the uninitiated falling behind, but these new stalwarts also don’t know what they don’t know when it comes to model risk.
A recent example is AI and hallucinations, though such initial outputs are well-understood by model developers and risk managers. A more tangible example is an unsuspecting driver, blind faith in a navigation app and a submerged vehicle. The Achilles Heel for corporate competitiveness is allowing this trend to continue, and should real disaster strike, boards of directors and chief executives will be exposed. Were they demonstrating the proper oversight?
How to address it: Changing the engagement model for the lay employee and board is priority one. The company’s technology lead, chief or otherwise, must undertake the responsibility of model evangelization on par with KnowBe4 and its revolutionization of information security risk training. Think: gamification, simplification, ubiquity and empowerment, starting with management and the board of directors. Two, agile (model) risk management must become the de facto, non-negotiable M.O. when building, adopting and implementing models that bear any material risk to financials or operations. Three, today’s boards of directors and chief executives must demand a frequent state of the IT union and bring to this elevated culture their own heightened level of understanding and credible challenge.
Risk Management Areas Addressed: Model Risk, Systemic Risk
VI. Operations
The Uncomfortable Vulnerabilities:
Details: The front office is not the only place for budget focus and fluency when before the board. A challenge companies face is ensuring budgets within the back office account for the corporate rather than their individual functional objectives. A common example is technology procurement and unintended redundancies, inefficiencies and failed adoption. Another challenge and post-covid Achilles Heel is fluency with global dynamics, which has, of late, led to companies scrambling to de-risk exposure to China and Ukraine, be it supply chains or business operations.
How to address it: Annual work plans is priority one. The Chief Financial and Operating Officers must establish a back office template and process for these individual functions to demonstrate how each will support the company’s strategic plan and mitigate its material risks. Two, a designated CFO or COO office must work with back office executives to ensure resource, technology, risk management and operational expenses are refined and then articulated up, holistically, to the board. Three, Risk Management must elevate geopolitical risk to its Enterprise Risk Management program, incorporate business continuity alternatives to higher risk locations and, as with Executive Management Cyber Resilience, practice incident agnostic resiliency.
Risk Management Areas Addressed: Geopolitical Risk, 3rd & 4th Party Risk, Financial Risk.
Conclusion
Managing risk effectively at the board, executive and functional levels requires a myriad of skills beyond the technical. Should any of the above vulnerabilities be exploited - by an action or inaction - any root-cause analysis will zero in on design and process. But make no mistake, performance, too, will receive its fair scrutiny. Accordingly:
Boards and chief executives that open their apertures and call for more attention to these vulnerabilities will yield tangible benefits:
Don't wait. Manage the uncomfortable.
[1] This is a nice explanation by Splunk of vulnerabilities, threats and risks in cybersecurity.
[2] A designated PMO to achieve this milestone might be worth his or her salt.
© 2023 Alliance of Business Lawyers. All rights reserved.